Here are 10 Ways Hackers Hack Debit Card And Withdraw Cash – Bypass OTP security verification, if you are looking for a way to hack someone’s credit/debit card bypassing OTP and withdraw money without traces then search no more. On this post you will be guided and you will learn how to hack credit card or debit card through advanced carding method on this 10 Ways Hackers Hack Debit Card And Withdraw Cash in few steps article, also learn how to clone credit card, how to clone debit card we have detailed on this article.
10 Ways Hackers Hack Debit Card And Withdraw Cash
To help you skip the long article, if you are looking for the software you will use to hack any debit card or hack any credit card kindly click here to get it, choose your operating system after purchasing it (windows, MacBook, Linux/mob all available.). Got questions? Contact our customer support using the contact button below the website.
Before advanced carding, there was carding and we will explain in details on this article, so pay attention.
What Is Carding?
Carding refers to the illegal activity of using stolen credit/debit card details (numbers, CVVs, expiry dates) to buy goods, often prepaid gift cards, to launder money and cover tracks (through buying of digital products or assets such as cryptocurrency),
Essentially fraudulent use of payment card info. It’s a cybercrime where fraudsters obtain card data, often via data breaches or phishing, and use it for purchases, making it a significant part of online fraud.
How Does Carding Works (Bank Card Fraud)?
Carding works through the following steps:
- Data Acquisition: Criminals get card numbers from data breaches, malware, or phishing scams.
- Purchase of Goods: They use these details to buy high-demand items (electronics, cryptocurrencies, gift cards) online.
- Money Laundering: Gift cards are preferred as they’re harder to trace and can be resold for cash.
- Dark Web Marketplaces: Stolen card data is also sold on underground forums.
Stolen Cards Acquisition (How To Buy Stolen Credit/Debit Cards)
There are a great many of methods to acquire credit card and associated financial and personal data. The earliest known carding methods have also included “trashing” for financial data, raiding mail boxes and working with insiders.
Some bank card numbers can be semi-automatically generated based on known sequences via a “BIN attack”. Carders might attempt a “distributed guessing attack” to discover valid numbers by submitting numbers across a high number of ecommerce sites simultaneously.
Today, various methodologies include skimmers at ATMs, hacking or web skimming an ecommerce or payment processing site or even intercepting card data within a point of sale network.[10] Randomly calling hotel room phones asking guests to “confirm” credit card details is example of a social engineering attack vector.
Resale Of Stolen Credit/Debit Cards
Stolen data may be bundled as a “Base” or “First-hand base” if the seller participated in the theft themselves. Resellers may buy “packs” of dumps from multiple sources. Ultimately, the data may be sold on darknet markets and other carding sites and forums.
specialising in these types of illegal goods. Teenagers have gotten involved in fraud such as using card details to order pizzas. On the more sophisticated of such sites, individual “dumps” may be purchased by zip code and country so as to avoid alerting banks about their misuse. Automatic checker services perform validation en masse in order to quickly check if a card has yet to be blocked. Sellers will advertise their dump’s “valid rate”, based on estimates or checker data. Cards with a greater than 90% valid rate command higher prices. “Cobs” or changes of billing are highly valued, where sufficient information is captured to allow redirection of the registered card’s billing and shipping addresses to one under the carder’s control.
Full identity information may be sold as “Fullz” inclusive of social security number, date of birth and address to perform more lucrative identity theft.
Fraudulent vendors are referred to as “rippers”, vendors who take buyer’s money then never deliver. This is increasingly mitigated via forum and store based feedback systems as well as through strict site invitation and referral policies.
Funds from stolen cards themselves may be cashed out via buying cryptocurrency, pre-paid cards, gift cards or through re-shipping goods through mules then e-fencing through online marketplaces like eBay.
Increased law enforcement scrutiny over reshipping services has led to the rise of dedicated criminal operations for reshipping stolen goods. Hacked computers may be configured with SOCKS proxy software to optimise acceptance from payment processors.
Money Laundering
The 2004 investigation into the ShadowCrew forum also led to investigations of the online payment service E-gold that had been launched in 1996, one of the preferred money transfer systems of carders at the time. In December 2005 its owner Douglas Jackson’s house and businesses were raided as a part of “Operation Goldwire”. Jackson discovered that the service had become a bank and transfer system to the criminal underworld. Pressured to disclose ongoing records disclosed to law enforcement, many arrests were made through to 2007.
However, in April 2007 Jackson himself was indicted for money laundering, conspiracy and operating an unlicensed money transmitting business. This led to the service freezing the assets of users in “high risk” countries and coming under more traditional financial regulation.
Since 2006, Liberty Reserve had become a popular service for cybercriminals. When it was seized in May 2013 by the US government, this caused a major disruption to the cybercrime ecosystem.
Today, some carders prefer to make payment between themselves with bitcoin, as well as traditional wire services such as Western Union, MoneyGram or the Russian WebMoney service.
Other Methods Or Related Cyber Frauds
Many forums also provide related computer crime services such as phishing kits, malware and spam lists. They may also act as a distribution point for the latest fraud tutorials either for free or commercially. ICQ was at one point the instant messenger of choice due to its anonymity as well as MSN clients modified to use PGP.
Carding related sites may be hosted on botnet based fast flux web hosting for resilience against law enforcement action. Other account types like PayPal, Uber, Netflix and loyalty card points may be sold alongside card details.
Logins to many sites may also be sold as a backdoor access apparently for major institutions such as banks, universities and even industrial control systems. For gift card fraud, retailers are prone to be exploited by fraudsters in their attempts to steal gift cards via bot technology or through stolen credit card information.
In the context of fraud, using stolen credit card data to purchase gift cards is becoming an increasingly common money laundering tactic. Another way gift card fraud occurs is when a retailer’s online systems which store gift card data undergo brute force attacks from automated bots.
Tax refund fraud is an increasingly popular method of using identify theft to acquire prepaid cards ready for immediate cash out. Popular coupons may be counterfeited and sold also. Personal information and even medical records are sometimes available.
10 Ways Hackers Hack Debit Card And Withdraw Cash
Theft and gift card fraud may operated entirely independently of online carding operations. Cashing out in gift cards is very common as well, as “discounted gift cards” can be found for sale anywhere, making it an easy sale for a carder, and a very lucrative operation.
The Google hacks, popularly known as Google dorks for credit card details, are also used often in obtaining credit card details.
Why go through the stress of carding when you can easily withdraw money from any debit card without trace, take out advance cash from stolen credit cards without any traces using “advanced carding”?
What Is Advanced Carding?
Advanced carding is the modern carding method that allows you to hack any credit or debit card, take out money (cash) without any trace or stress of having the money without any law enforcement hunting for you.
Looking For The PACS.008 MX System? CLICK HERE!
How Does Advanced Carding Work?
Advanced carding in ten easy steps, within 5 minutes you can get done with the process if you do it right or have the necessary details and equipment you need to pull this off, the following are advanced carding steps:
- Step 1: get the card info you want to pull or withdraw money from, (required info are Card number, CVV, Expiry date and and card holder’s name. Billing address is optional but we recommend you have it handy).
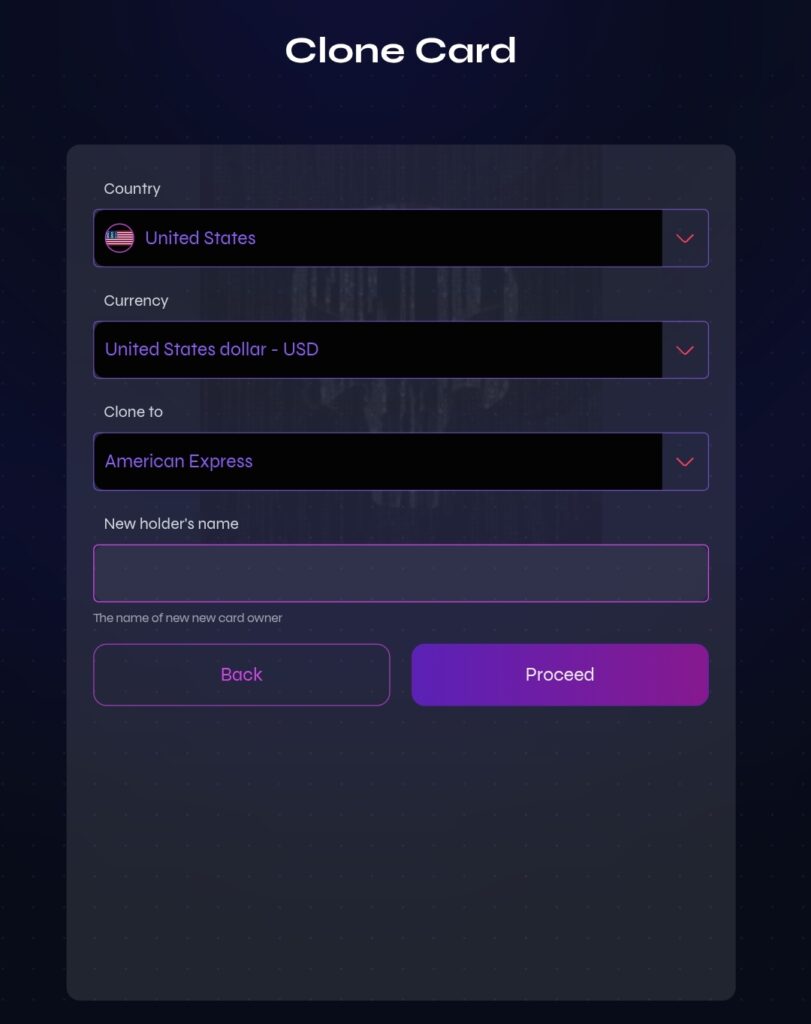
- Step 2: Initiate the cloning of the card into a new one, original card will won’t be affected. The cloning process is explained below,
- Step 3: Copy the cloned card details and use cardpulling,
- Step 4: choose card type in the cardpulling, choose country and enter card details.
- Step 5: Enter amount you want to pull out of the card after entering the card details.
- Step 6: Proceed and choose to pull the funds/cash through the dedicated wallet.
- Step 7: Pull the money from the card successfully after clicking confirmation button.
- Step 8: Head to the wallet, add your crypto wallet address but note that only USDT is recommended for quick confirmation on the network (TRC20, ERC20 and BEP20 networks supported).
- Step 9: Head to the convert section, convert the money to usdt crypto (conversion commission applies).
- Step 10: Final step, head to the withdrawal section, click withdraw, enter a specific amount or all, choose receiving address, select priority network and click the withdraw button.
The above are 10 Steps To Clone Credit/Debit Card And Withdraw Money Bypassing OTP, also explained in graphic images below, kindly have a look.
STEP ONE (1)
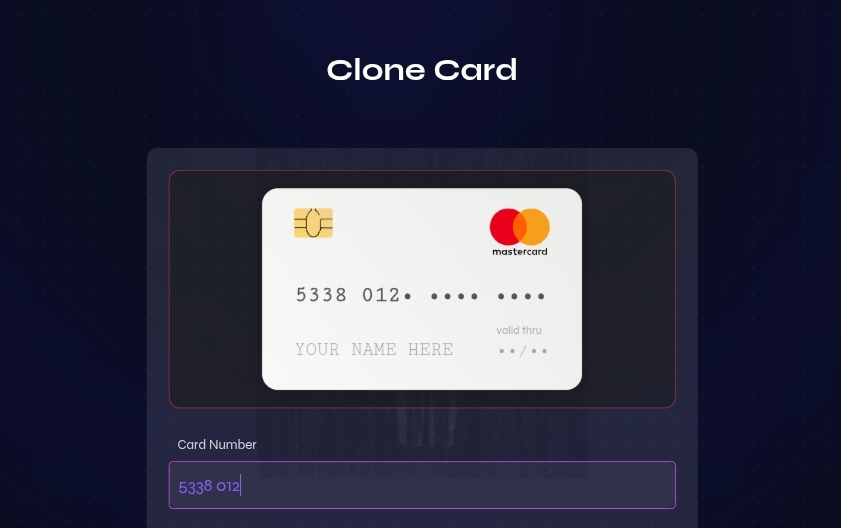
STEP TWO (2)
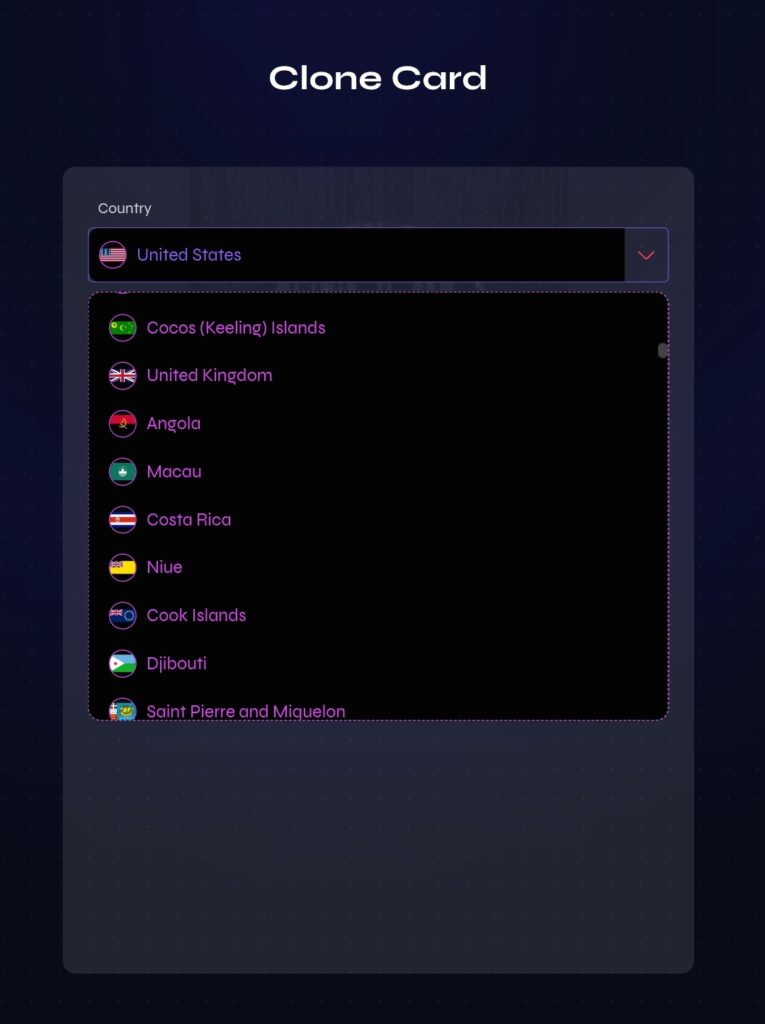
STEP THREE (3)
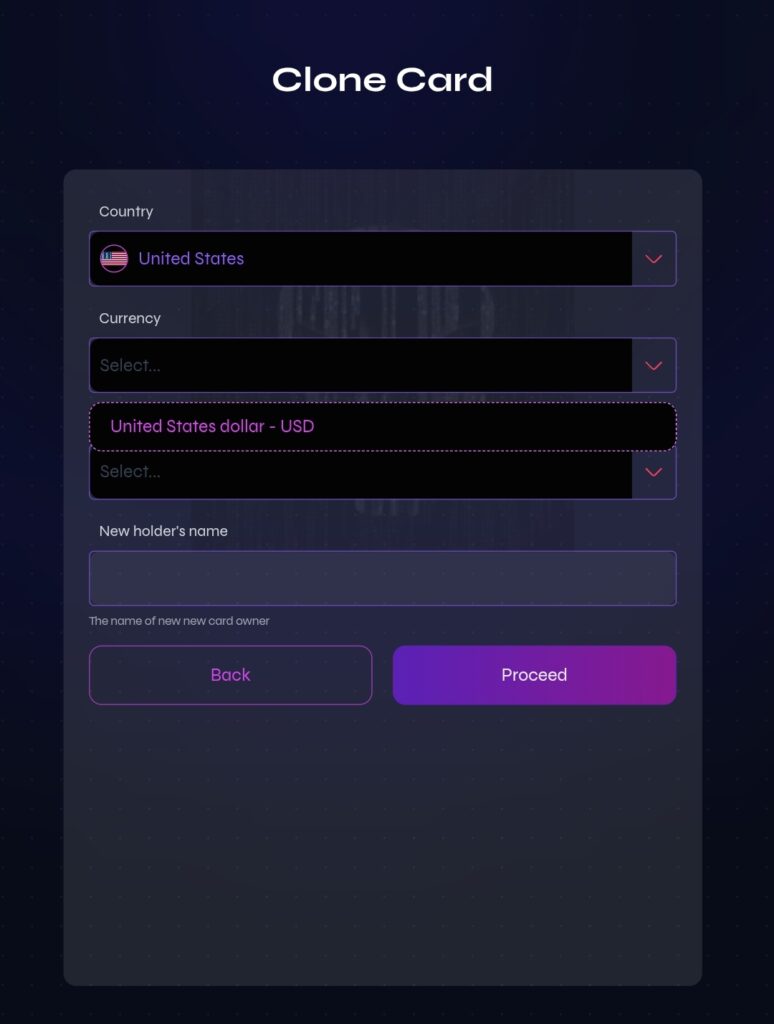
STEP FOUR (4)
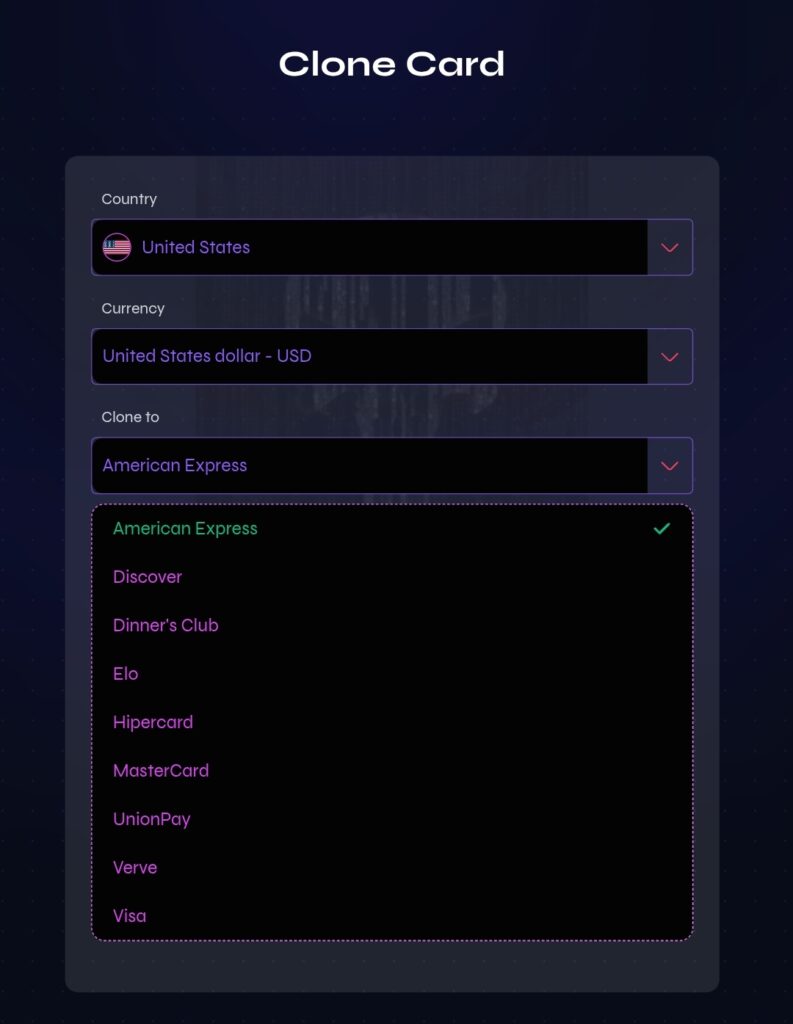
STEP FIVE (5)
That is all on 10 Ways Hackers Hack Debit Card And Withdraw Cash Bypassing OTP verification, for more info or inquiry kindly contact our support.
If you find this article on “10 Ways Hackers Hack Debit Card And Withdraw Cash” helpful, kindly share it.


Leave a Reply